Review of the Operationalization of the Security of Canada Information Sharing Act
Canada Border Services Agency
Canadian Security Intelligence Service
Global Affairs Canada
Immigration, Refugees and Citizenship Canada
Royal Canadian Mounted Police
Final Report 2017
Main Points
What we examined
The Security of Canada Information Sharing Act (SCISA)Footnote 1 came into force on August 1, 2015. Its stated purpose is to encourage and facilitate the sharing of information between federal institutions for purposes of national security. Under section 5(1) of the Act, a federal institution may, on its own initiative or on request, disclose information to one of 17 designated departments or agencies, if that information is relevant to the receiving institution’s jurisdiction or responsibilities in respect of activities that undermine the security of Canada. An activity that “undermines the security of Canada” is defined within section 2 of SCISA.
We examined the information sharing activities under SCISA for the one year period of August 1, 2015 through July 31, 2016. Five federal entities were selected for review – all of which had reported disclosures or receipts during this period: the Canadian Security Intelligence Service (CSIS), the Royal Canadian Mounted Police (RCMP), the Canada Border Services Agency (CBSA), Global Affairs Canada (GAC), and Immigration, Refugees and Citizenship Canada (IRCC).
In addition to examining the disclosures under SCISA, we reviewed institutional policies, practices and internal controls supporting those disclosures. Information sharing agreements were also reviewed, as well as the extent to which institutions were generally engaged in the evaluation and mitigation of privacy risks related to the exchange of information under SCISA.
Disclosures under SCISA
Disclosures of information
5 (1) Subject to any provision of any other Act of Parliament, or of any regulation made under such an Act, that prohibits or restricts the disclosure of information, a Government of Canada institution may, on its own initiative or on request, disclose information to the head of a recipient Government of Canada institution whose title is listed in Schedule 3, or their delegate, if the information is relevant to the recipient institution’s jurisdiction or responsibilities under an Act of Parliament or another lawful authority in respect of activities that undermine the security of Canada, including in respect of their detection, identification, analysis, prevention, investigation or disruption.
Why we conducted this review
Balancing Canada’s national security interests with Canadians’ right to privacy is critically important. We recognize that greater information sharing may sometimes lead to the identification and suppression of security threats. However, institutions sharing information must also take into consideration the privacy of those to whom the information belongs. In our view, information sharing must be undertaken with care and with regard for the potential impacts of sharing on individuals. This is particularly true for law abiding citizens - those who are not the subject of an investigation, but who may be unknowingly immersed or implicated in the government’s information sharing activities. Personal information, if mishandled, could result in serious impacts on the privacy, freedom, reputation, and livelihood of an individual and his or her family.
The threshold for information sharing is of central importance to striking the right balance in the protection of privacy rights. For that balance to be achieved, personal information should only be shared where there is a demonstrable need to do so, and where such information sharing is tightly controlled so as to minimize the detrimental effects on individuals. Moreover, institutions involved in the sharing of personal information under SCISA should be responsible and accountable for the proper handling of that information in accordance with legal and policy requirements.
What we found
Our review found significant procedural deficiencies in the operationalization of the Act. We expected institutions engaged in the sharing of information under SCISA to have developed and implemented systems or processes for the monitoring and recording of information exchanged under the Act. Such systems or processes are critical in supporting good governance practices and in facilitating operational oversight over personal information exchanges.
There was no formal overarching reporting structure in place to capture the exchange of information under the Act. Record keeping practices varied among institutions – and in one case, within the same institution – and not all disclosures or receipts of information under SCISA were recorded. As a result, we were not provided with complete and reconciled records of information sharing activity under the Act by all institutions. Consequently, our Office could not review the full extent of information sharing under SCISA and therefore could not assess whether or not all disclosures under SCISA were compliant with the Privacy Act.
Records, when kept, did not consistently meet the government’s own guidelines or expectations, as set out in the Public Safety Canada Deskbook: A Guide to Responsible Information Sharing. Although there is currently no legal duty to keep a record of SCISA disclosures, without such records (and good recordkeeping practices more generally) it is difficult to hold institutions accountable for the information they are sharing under the Act. It is equally difficult for institutions to demonstrate their compliance with SCISA’s information sharing requirements, and those under the Privacy Act,Footnote 2 making governance, oversight and an evaluation of the Act’s effectiveness challenging.
Virtually all disclosures under SCISA to date have been directed to CSIS or the RCMP. Of the disclosure records presented for our review, most were in response to formal information requests, related to individuals who were the subjects of investigations, and the information shared did not exceed the parameters of the requests. In addition, many of the pro-active disclosures were preceded by a discussion between the institutions involved in the exchange. In short, the vast majority of disclosures met the threshold for information sharing under the Act.
While not systemic in nature, we did find instances where an institution had disclosed information about family members of individuals who were the subjects of investigations, and for which there was no evidence that such information was relevant to the jurisdiction or authority of the receiving institution in respect of an activity that would undermine the security of Canada. The receiving institution did not review the information upon receipt prior to retaining it. The information was not vetted by either entity to ensure it met the threshold for disclosure under the Act.
SCISA provides institutions with the authority to disclose sensitive information about individuals that is collected in the course of the disclosing institution’s ordinary operating activities. Where that information may be used by the receiving institution in a decision-making process that directly affects the individual, we expected institutions disclosing and receiving information pursuant to the Act to have conducted privacy impacts assessments (PIAs) in relation to those activities. None of the five institutions have done so.
SCISA’s preamble makes express reference to the need for institutions to share information under the Act in a manner that is consistent with the Canadian Charter of Rights and Freedoms and the protection of privacy. This means ensuring, among other things, that information exchanged is limited to what is necessary and that information, once shared, is subject to appropriate restrictions, including limitations on use, disclosure and retention. It also requires that institutions ensure that any information they share is relevant to an activity undermining the security of Canada, and that it is in keeping with the receiving institution’s authorities. For institutions receiving information under SCISA, each piece of personal information to be collected should relate directly to and be demonstrably necessary to the institution’s operating programs or activities.
Absent appropriate recordkeeping and internal controls, the use of SCISA’s information sharing authorities will remain a threat to the privacy of individuals. Whereas SCISA’s preamble underscores the importance of privacy, not all institutions sharing personal information appear to have formally considered the privacy impacts of their information sharing practices under the Act.
Introduction
About the Security of Canada Information Sharing Act
- Threats to Canada’s national security range in kind from terrorism to cyber-attacks and espionage. Information about such threats can emanate from different sources. In order to effectively respond to threats, the Government of Canada believes that information pertaining to national security should be sourced from all federal institutions, and shared with designated institutions so as to better understand and assess risks to the national interest.
- In January 2015, Bill C-51 (otherwise known as the Anti-Terrorism Act, 2015Footnote 3) was tabled in Parliament, introducing, among other laws, the Security of Canada Information Sharing Act (SCISA). SCISA aims to improve the effectiveness and timeliness of information sharing between federal institutions for national security purposes. It purports to do so, in part, by establishing an explicit authority for all federal government institutions to disclose information – including personal information – to 17 designated national security mandated institutions listed in Schedule 3 of that Act. The Act authorizes the disclosure of information to the designated institutions if it is relevant to the recipient institution’s jurisdiction or responsibilities in respect of activities that undermine the security of Canada.
| Canada Border Services Agency |
| Canada Revenue Agency |
| Canadian Armed Forces |
| Canadian Food Inspection Agency |
| Canadian Nuclear Safety Commission |
| Canadian Security Intelligence Service |
| Communications Security Establishment |
| Department of Citizenship and Immigration (now Immigration, Refugees and Citizenship Canada) |
| Department of Finance |
| Department of Foreign Affairs, Trade and Development (now Global Affairs Canada) |
| Department of Health |
| Department of National Defence |
| Department of Public Safety and Emergency Preparedness |
| Department of Transport |
| Financial Transactions and Reports Analysis Centre of Canada |
| Public Health Agency of Canada |
| Royal Canadian Mounted Police |
Early concerns
- Prior to its implementation, the Office of the Privacy Commissioner of Canada (OPC) raised a number of concerns regarding SCISA. Primary among those concerns was the potential scale of information sharing activities that could be authorized under the Act. Unprecedented sharing, when combined with the potential use of analytics, could result in large amounts of personal information being analyzed to spot trends, to predict behaviour, and to make connections about individuals who may never pose a threat to the security of Canada.
- Also of concern was the low threshold for sharing information under SCISA. Under the Act, for information to be shared, it need only be ‘relevant’ to the jurisdiction of the recipient institution or its responsibilities in respect of acts that undermine the security of Canada, rather than necessary to its mandate and proportional to the national security objective at hand. In our view, an application of the relevance standard could provide national security agencies with almost limitless powers to monitor and profile all Canadians – not just actual terrorist suspects. The Act also lacks clear retention and destruction obligations for organizations, and it does not require written agreements to support the proper sharing of information.
Focus of our review
- In 2015, the OPC began a phased approach to the review of the operationalization of SCISA. The first phase was initiated in January 2016 with a view to informing stakeholders (particularly the Parliament of Canada) of the extent to which information was being shared under SCISA. To that end, a survey was issued to all 17 institutions listed in Schedule 3 of the Act authorized to both receive and disclose information, and to the 111 federal institutions authorized to disclose information under SCISA.
- In responding, only 5 of the 17 Schedule 3 institutions reported having received and/or disclosed information under SCISA. They included: the Canada Border Services Agency (CBSA), the Canadian Security Intelligence Service (CSIS), Immigration, Refugees and Citizenship Canada (IRCC), Global Affairs Canada (GAC), and the Royal Canadian Mounted Police (RCMP).
- Whereas the first phase of our review focused on the extent of information sharing under SCISA, the second phase examined the manner in which information was being shared under the Act. Its purpose was to identify early and emerging privacy issues in relation to SCISA’s operationalization, and to more closely consider the personal information handling practices of institutions sharing information under the Act. Of particular interest was the manner in which information relating to third-parties unrelated to an investigation was being treated.
- To this end, we reviewed all documented exchanges of information under SCISA for the period of August 1, 2015 through July 31, 2016. We also reviewed the extent to which institutions were generally engaged in the evaluation and mitigation of privacy risks related to the exchange of information under SCISA, as well as the internal controls in place to ensure that personal information disclosed or received under SCISA was being handled in compliance with the Privacy Act.
- While our work was undertaken with a view to determining whether SCISA disclosures were relevant to an active investigation, as related to an activity that could undermine the security of Canada, we did not evaluate or assess on-going uses of that information by recipient departments or compliance with caveats placed on the shared information.
- Additional information about the examination can be found in the ‘About the Review’ section of this report.
Observations and Recommendations
- The adoption of a phased approach to reviewing SCISA’s operationalization was intended to provide stakeholders with an early understanding of how the Act was working. Its impact on the privacy rights of individuals may take several more years to fully evaluate.
- Although most federal institutions are authorized to disclose information under the Act – and 17 institutions are authorized to receive information – our review found that virtually all disclosures under the Act to date have been directed to CSIS or the RCMP. Of the files presented for our review, the vast majority were in response to formal information requests, related to individuals who were the subject of investigations, and the information provided did not exceed the parameters of the requests. Many of the pro-active disclosures were preceded by a discussion between the institutions involved in the exchange. In short, the threshold for disclosure under SCISA was met in the vast majority of the files we reviewed.
- We did, however, find instances where disclosures included information about family members of individuals who were the subjects of investigations, and for which there was no evidence that such information was relevant to the jurisdiction or responsibilities of the recipient institution in respect of an activity that would undermine the security of Canada. Moreover, we were unable to reconcile a number of reported disclosures and receipts of information; therefore, we could not review and assess the full extent of information sharing under the Act.
- SCISA has been in place since August 2015, and only five institutions have been engaged in information sharing activities under the Act thus far; however, our recommendations are relevant to all institutions subject to the legislation.
Recordkeeping is incomplete and there is no formal structure in place to track and monitor the exchange of information under SCISA.
- In our submissions to Parliament regarding SCISA, we underscored the need for good governance and strong oversight over the sharing of personal information. Good governance helps to ensure that institutions sharing information are accountable for their disclosure of personal information, and that they remain transparent about information being exchanged with federal counterparts for reasons of national security.
- SCISA itself emphasizes the need for good governance and accountability over the sharing of information. Paragraph 4(d) of the Act states that the sharing of information should be guided by the principle that “the provision of feedback as to how shared information is used and as to whether it is useful in protecting against activities that undermine the security of Canada facilitates effective and responsible information sharing”. In the same way, SCISA’s preamble states that Government of Canada institutions are “accountable for the effective and responsible sharing of information.”
- Accountability and responsibility, in our view, begins with good recordkeeping. Without a record of what is being disclosed, to whom, and for what purposes, it is impossible to determine whether or not a given disclosure is appropriate in the circumstances. The absence of good records also impedes the government’s ability to oversee, measure and assess the Act’s effectiveness in achieving its intended goals.
- In the course of our review, we asked institutions to report the number of times they had disclosed information under SCISA. We also asked them to confirm the number of times that they had received information pursuant to the Act. Collectively, the institutions reported 97 receipts of information and 118 disclosures under the Act during the period covering August 1, 2015 through July 31, 2016. The following table summarizes reported information sharing activity.
Table 2: Summary of Disclosures and Receipts of Information under SCISA Institution Disclosed information under SCISA Recipient of information under SCISA Canada Border Services Agency Yes Yes Canadian Security Intelligence Service Yes Global Affairs Canada Yes Immigration, Refugees and Citizenship Canada Yes Yes Royal Canadian Mounted Police Yes Yes Information sharing activity 118 97 - As reflected above, the total number of files institutions reported as having been disclosed under SCISA did not equal the total number of files acknowledged as having been received. Moreover, the disclosure events reported did not align with the actual number of files presented for our review; we were provided access to 98 receipt and 130 disclosure files. Although our Office attempted to reconcile recorded disclosures and receipts, we were unable to do so in all cases. Consequently, we were unable to review and assess the full extent of information sharing under the Act. In some cases, discrepancies appeared to be attributed to the following:
- information sharing activity initially reported as having occurred under SCISA was subsequently determined not to have transpired;
- although SCISA was cited as the disclosure authority, the sharing activity was undertaken pursuant to another legislative authority; and
- a nil response (i.e., confirmation that the responding institution did not possess information on the subject of a request) was deemed a disclosure by only one of the two entities involved in the exchange.
- While we found no evidence of any deliberate attempts to withhold records exchanged, the variance does highlight a serious inconsistency in recording practices across government in relation to SCISA exchanges. It also speaks to our concerns over accountability. Inconsistent and incomplete reporting of SCISA events impedes effective oversight with respect to the Act’s administration. It also impedes the proper evaluation of SCISA’s effectiveness in achieving its intended goals.
- In our view, the absence of a consistent government-wide reporting mechanism to track the exchange of information under SCISA is concerning. As previously stated, without a clear and reliable record of what is being disclosed, to whom, and for what purposes, it is difficult to assess an institution’s compliance with the Act. It is also difficult to determine whether the number of reported disclosures under SCISA across government is accurate and complete. This applies to the records that were provided for our review.
- Beyond the absence of a standardized reporting process for SCISA disclosures and receipts, we were also concerned about the apparent incompleteness of records relating to known or reported disclosures. In many cases, the recordkeeping practices of the institutions we reviewed did not meet the minimum expectations or recommendations of the Government of Canada itself.
- To support the implementation of SCISA, Public Safety Canada issued a Deskbook: A Guide to Responsible Information Sharing (the Deskbook). The Deskbook was developed as an authoritative reference for applying the Act. Among other things, the guidance provided therein encourages institutions to consider and document the following prior to disclosing information under SCISA:
- The institution’s own legislative authorities, and any legal restrictions that may apply to the disclosure of personal information;
- The receiving institution’s authority to receive information under SCISA;
- The nature of the information, and whether the information is relevant to carrying out the duties or functions of the receiving institution in relation to an activity that undermines the security of Canada;
- The sensitivity of the information and whether it requires special handling requirements.
- While the inclusion of all the above elements may not be relevant to each and every disclosure, we would have expected institutions to have documented in detail the rationale for disclosures of personal information under SCISA. Such a practice is particularly important in relation to the disclosure of information about individuals who are not the subject of an investigation.
- Under SCISA, information may only be shared if it is “relevant to the recipient institution’s jurisdiction or responsibilities… in respect of activities that undermine the security of Canada”.Footnote 4 As such, before disclosing information under SCISA, institutions must be satisfied that the information relates to an activity that undermines the security of Canada, and that it is relevant to the recipient institution’s responsibilities in respect of that activity.
- On many of the files reviewed, we saw little documented evidence of the application of any established criteria for the disclosure of personal information under SCISA. While we accept that an application of the threshold or criteria for sharing may, in many cases, have been satisfied through discussions between institutions, we would have expected the essence of those discussions and subsequent analysis to have been documented, so as to demonstrate that the decision to share information had been rendered on a reasonable basis.
Recommendation 1:
To encourage good governance over the sharing of personal information under SCISA, and to improve accountability and transparency with respect to its use, institutions should, in collaboration with their partners, implement a formal and standardized process for the identification and recording of information sharing activities under the Act.
Recommendation 2:
Recordkeeping practices of disclosing institutions should meet the minimum standards set out in Public Safety Canada’s Deskbook, and include a detailed description of how the facts of a given situation meet the legal grounds for disclosure.
Risk management activities have not been undertaken to identify and mitigate privacy risks related to the Act’s operationalization.
- Under the Government of Canada’s Policy on Privacy Protection, federal institutions subject to the Privacy Act are required to develop, maintain, and publish privacy impact assessments (PIAs) in relation to new programs and services involving personal information.Footnote 5 Institutions must initiate a PIA for a program or activity when personal information is used (or is intended to be used) in a decision-making process that directly affects the individual. PIAs are also required where an institution makes substantial modifications to an existing program or activity involving personal information.
- We recognize that the operational impacts of SCISA are likely to vary by institution. Many federal institutions were sharing information with each other for national security purposes well before SCISA’s introduction and, as such, have (or ought to have) formally evaluated the risks of sharing of data for national security purposes. In other cases however, the sharing or receipt of personal information for national security purposes may be altogether novel, particularly with respect to the many institutions who have newly granted authorities under SCISA, or where national security matters are not central to the institution’s mandate. As a result, many institutions that are expected to disclose personal information under SCISA are unlikely to have formal policies and practices in place to support the exchange of information under the Act.
- Whereas SCISA provides institutions with the authority to disclose personal information to one of 17 receiving institutions, and where that information may be used by the receiving institution in a decision-making process that directly affects the individual, institutions sharing information under SCISA ought to be identifying and assessing the privacy impacts associated with any such sharing prior to exercising its authorities under the Act. Institutions with PIAs already in place should update those assessments to the extent that SCISA impacts the manner in which information is collected, used, or disclosed. Absent the performance of a formal PIA or PIA update, it is unclear to us how institutions intend to assess and ensure compliance with their legal and policy requirements related to the administration of the Privacy Act.
- Inquiries were made to determine whether the five entities selected for review had undertaken a PIA—or amended a pre-existing assessment—in relation to SCISA. In responding, two reported that PIAs were not required, one institution had not identified a need for a PIA to date, and the remaining two organizations have deferred proceeding with assessments pending further review.
- In summary, the five institutions have not undertaken any specific risk management activities to identify and mitigate privacy risks related to SCISA’s operationalization, notwithstanding the material impacts that the Act may potentially have on the kinds and extent of information sharing that may occur between institutions and across the Canadian government pursuant to the Act.
- In our view, the disclosure of information for purposes other than that for which it was collected could constitute a substantial modification to a program or activity of an institution, thus triggering the requirement for a PIA in instances where one did not previously exist (or an amendment to a pre-existing one). Although collection authorities will not change for recipient institutions as a result of SCISA, it is clearly intended that more and different information may be received by institutions than prior to the enactment of the Act, which would similarly constitute a substantial modification to a program or activity.
Recommendation 3:
In keeping with the requirements of the Government of Canada’s Policy on Privacy Protection, and its supporting Directive on Privacy Impact Assessment, institutions sharing or receiving personal information pursuant to SCISA should undertake a formal assessment of the privacy impacts associated with its operationalization.
Some internal controls need to be improved to help ensure the proper handling of personal information
- Under the Policy on Privacy Protection, federal institutions are required to establish practices for the sound handling of personal information under their control. Such practices are intended to ensure that the requirements of the Privacy Act are properly and consistently administered. In support of the Policy, the Government of Canada has established a Directive on Privacy Practices.Footnote 6 It sets out more detailed practice requirements, including the need for internal controls for the management of personal information.
- In the course of our review, we assessed the extent to which institutions had internal controls in place to manage and mitigate privacy risks associated with the exchange of personal information under SCISA. By internal controls, we mean processes and/or policies designed to help achieve compliance with operational objectives and statutory requirements. In conducting our work, we reviewed copies of policies supporting the handling of personal information. We also reviewed internal processes by which personal information was shared and received.
- Under SCISA, the sharing of personal information must be targeted and specific. Each element of personal information disclosed must be relevant to the receiving institution’s jurisdiction or responsibilities in respect of an activity that undermines the security of Canada. Conversely, under section 4 of the Privacy Act, government institutions shall not collect personal information unless it relates directly to an operating program or activity of the institution. Furthermore, the Government of Canada’s Directive on Privacy Practices states that institutions receiving information must limit their collection of personal information to that which is demonstrably necessary.Footnote 7
- Whereas the CBSA, CSIS, RCMP, GAC and IRCC are all authorized to both disclose and receive personal information under SCISA, we expected them to have designed and implemented controls to help ensure that the information-handling practices related to personal information they were sharing or receiving under SCISA complied with their statutory and policy obligations regarding privacy. We also expected institutions to have mechanisms in place to respect and enforce limitations on the ongoing use, disclosure and retention of personal information, if any, once received from another institution.
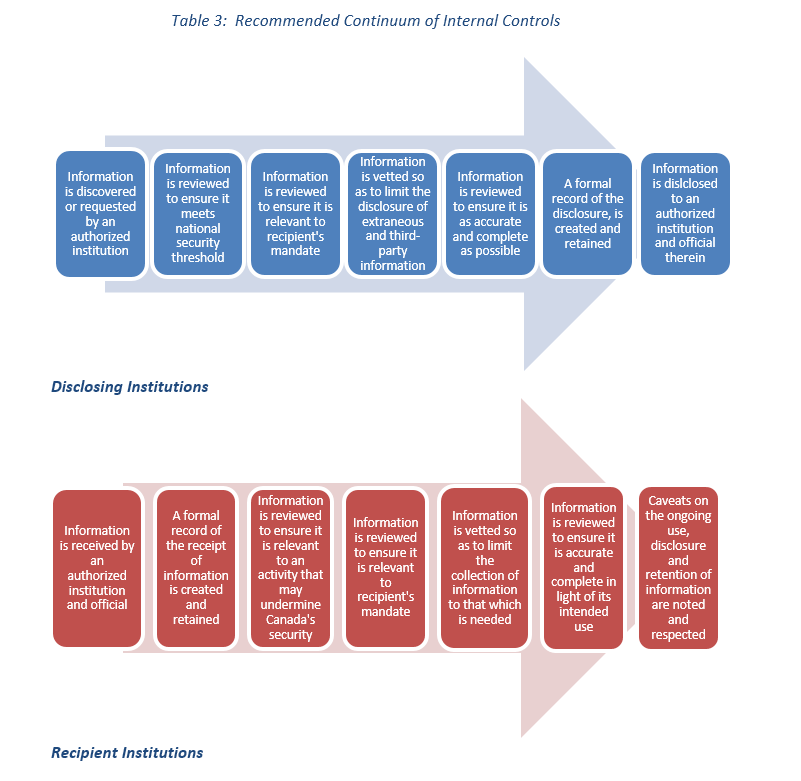
Text version
Table 3: Recommended Continuum of Internal Controls
Disclosing Institutions
- Information is discovered or requested by an authorized institution
- Information is reviewed to ensure it meets national security threshold
- Information is reviewed to ensure it is relevant to recipient's mandate
- Information is vetted so as to limit the disclosure of extraneous and third-party information
- Information is reviewed to ensure it is as accurate and complete as possible
- A formal record of the disclosure, is created and retained
- Information is dislclosed to an authorized institution and official therein
Recipient Institutions
- Information is received by an authorized institution and official
- A formal record of the receipt of information is created and retained
- Information is reviewed to ensure it is relevant to an activity that may undermine Canada's security
- Information is reviewed to ensure it is relevant to recipient's mandate
- Information is vetted so as to limit the collection of information to that which is needed
- Information is reviewed to ensure it is accurate and complete in light of its intended use
- Caveats on the ongoing use, disclosure and retention of information are noted and respected
- Sound policies are essential to protect organizational assets, including personal information. They establish accountability and associated responsibilities, and provide the mechanism through which security and privacy protection are integrated into day-to-day operations. The absence of well-defined policies may result in inconsistent and inadequate information-handling practices that place privacy at risk.
- Of the five institutions selected for examination, four have implemented policies to govern SCISA-related information sharing. The remaining entity had a directive in place for the exchange of information with one partner. At the time the review concluded, the entity had not developed a policy to support the broad implementation of SCISA.
- We expected that, at minimum, policies would include core elements that addressed the legislative threshold for sharing under the Act, institutional discretion, recordkeeping, accountability and oversight. A number of these elements were absent in some of the policies we reviewed; our analysis in this regard is provided below.
Table 4: Summary of policies governing information sharing under SCISA Core element Number of policies with core element contained therein Authorities Threshold for disclosing information under SCISA 4 of 5 Activities excluded from the definition of “activities that undermine the security of Canada” 3 of 5 Legislative prohibitions or limitations 4 of 5 Institutional discretion – disclosures are not mandatory 4 of 5 Disclosure of information Designated entities authorized to receive information under SCISA 4 of 5 The Canadian Charter of Rights and Freedoms and the protection of privacy as considerations in the disclosure decision-making process 4 of 5 Disclosure requirements (relevant and necessary) 3 of 5 Requirement for caveats (e.g., data reliability, limitations on the use, disclosure and retention of information shared, safeguarding) 4 of 5 Receipt of information Review of in-bound disclosures for relevancy and necessity 2 of 5 Handling of information that does not meet legislative threshold 2 of 5 Respect for caveats placed on information by disclosing institution 3 of 5 Record keeping Recording/tracking of disclosures/receipt of information under SCISA for accountability and transparency 4 of 5 Retention of records related to disclosures (e.g., date, information disclosed, to whom, for what purpose, analysis undertaken in support of disclosure) 4 of 5 Information sharing agreements Establishment of written agreements for information sharing under SCISA 1 of 5 Accountability and oversight Officials designated to authorize to disclosures under SCISA 3 of 5 Officials designated to receive information under SCISA 4 of 5 - In addition, we found that some institutions did not have formal controls in place to ensure that all policy requirements were being met. In particular, we noted one institution did not initially have a control mechanism in place to ensure that all information being disclosed was relevant to an activity that would undermine the security of Canada. Similarly, the recipient institution did not have controls in place to ensure that each element of personal information it was collecting was directly related or demonstrably necessary to the institution’s program or activities. In a number of cases, the absence of such controls allowed for the exchange of personal information belonging to third parties who may not pose a threat to the security of Canada. More generally, in the absence of certain record keeping practices, we were unable to verify whether other controls were in place and working as intended.
Recommendation 4:
Institutions should ensure that policies are in place to govern all information sharing activity under SCISA.
Recommendation 5:
Institutions should review and, where appropriate, adjust internal governance instruments to ensure that information sharing under SCISA complies with legislative requirements.
Recommendation 6:
Institutions should ensure that policies governing information exchanges under SCISA are supported by commensurate internal controls.
Recommendation 7:
Institutions should review disclosures received under SCISA to ensure that the information contained therein is relevant to its jurisdiction or responsibilities in respect of activities that undermine the security of Canada, and not retain any information that does not meet that threshold.
- Government of Canada guidance recommends that federal government institutions prepare written agreements for the sharing of personal information. Such agreements serve as a record of understanding between parties with respect to data exchanges and help to outline the terms and conditions under which personal information may be shared between them.
- In addition to having formal policies and internal controls governing the handling of personal information under SCISA, we expected institutions active in the sharing of information to have entered into written information sharing agreements (ISAs). The Privacy Commissioner has advocated that written information sharing agreements be required by law,Footnote 8 and that they should, at a minimum: define the specific elements of personal information to be shared; define the specific purposes for the sharing; and, limit secondary uses and onward transfer. These elements have been incorporated into the table below.
- Three institutions disclosed information under SCISA during the review period. Of these, two have ISAs with recipient institutions. The third institution has an ISA in place with only one of the two institutions to which it disclosed information.
- As part of our review, we obtained and reviewed the ISAs for privacy protections. As a benchmark for evaluation, we used the Government of Canada’s Guidance on Preparing Information Sharing Agreements Involving Personal Information.Footnote 9 It sets out the terms and conditions that institutions should include in all agreements governing the sharing of personal information.
- In our view, ISAs between entities ought to be sufficiently robust and comprehensive so as to ensure that foreseeable risks related to the exchange of personal information are appropriately identified and mitigated. To this end, institutions should ensure that a minimum set of privacy provisions are built into ISAs supporting SCISA. Although the purposes for sharing were defined within the ISAs reviewed, we identified a number of gaps in what we consider to be key privacy protections. Our observations in this regard are summarized below.
Table 5: Assessment of Core Elements in Information Sharing Agreements Privacy Protection Number of ISAs with the provision included therein Specific purposes for sharing are defined All Establishes the methods or procedures that will be used to share information 3 of 5 The specific elements of personal information to be shared are defined 3 of 5 Limits are placed on secondary uses 2 of 5 Limits are placed on onward transfers (disclosures) 3 of 5 Identifies the steps that will be taken to ensure the personal information is accurate, complete and up to date 3 of 5 Specifies how long the information is to be kept None Specifies who has legal control of the shared personal information None Includes key administrative, technical and physical safeguards and controls that are required to prevent unauthorized access, use or further disclosure 3 of 5 States that, in the event of a privacy breach (an unauthorized use or disclosure of the information), the party in breach will notify the party that shared the information 3 of 5 - A number of the ISAs were silent on the mechanisms or methods for exchanging personal information, data accuracy and completeness, as well as obligations for the safekeeping and safe-handling of personal information. Similarly, provisions governing data retention and control over the information shared were absent in all of the agreements reviewed.
- In our view, information sharing agreements are critically important in supporting the exchange of personal information under SCISA, particularly so in the absence of formal regulations to support the Act’s administration. When properly drafted, they help to clarify the rights and obligations of the parties, to define custody and control issues, and to establish protocols for addressing problems and incidents. They also provide positive awareness and instructions for federal employees charged with information sharing responsibilities. Most importantly, information sharing agreements help to ensure that institutions sharing and receiving information are in compliance with the requirements of the Privacy Act.
Recommendation 8:
Institutions should ensure that information sharing activity under SCISA is subject to a written agreement.
Recommendation 9:
Institutions should ensure that written agreements governing the disclosure and receipt of information under SCISA include appropriate privacy protections.
Conclusions
- In conducting our review, we expected institutions sharing information under SCISA to have developed and implemented formal recordkeeping systems so as to allow for the consistent tracking and monitoring of disclosures and receipts of information under the Act. This practice is in keeping with the Government of Canada’s own guidance on the operationalization of SCISA. Proper recordkeeping is critical for ensuring good governance, and for encouraging accountability and transparency with respect to personal information disclosures.
- We also expected institutions to have engaged in appropriate risk management activities so as to identify and minimize the privacy impacts associated with the exchange of information under the Act. To the extent that SCISA impacts the kinds of information institutions are disclosing, and/or the manner or purposes for which that information is shared, institutions have an obligation to ensure that privacy issues are appropriately identified, assessed and resolved before disclosing any personal information.
- Finally, we expected all institutions to have appropriate internal controls—including policies and ISAs—in place to manage and mitigate privacy risks associated with the sharing of information under SCISA. It would also include controls to limit the disclosure of information relating to third parties who are not the target or subject of an investigation and to ensure that information is appropriately vetted upon receipt.
- Based on our review, not all of our expectations have been met. Additional work is required to ensure that information sharing activities under the Act are well documented for transparency and accountability, and that the privacy impacts associated with the Act’s operationalization are fully considered and addressed.
- In reflecting on the overall findings of our review, we note that many of our initial concerns with respect to SCISA continue to be relevant. At the outset, our Office expressed concerns that the Act might lead to the wide sharing of personal information among government of Canada institutions. We found that not all disclosures under the Act could be reconciled. Thus, a full accounting of the information sharing activity under the Act remains unknown.
- Absent formal and standardized recordkeeping of disclosures government-wide and the implementation of robust internal controls, the risk of unauthorized and excessive sharing of personal information remains. And while the vast majority of the files we reviewed showed that the threshold for disclosure was satisfied, that standard of relevance is extremely low. The fact that the Act establishes such a low threshold and it is silent on the proper handling of information subject to disclosure means that a real possibility exists that SCISA will be used as a means to share information with respect to individuals who may not pose a threat to the security of Canada.
About the review
Authority
Section 37 of the Privacy Act empowers the Privacy Commissioner to undertake compliance reviews of the personal information management practices of federal entities listed in the Schedule to the Act.
Objective
The objective of our review was to verify whether information sharing activities of select institutions complied with the provisions of SCISA. It also served to assess whether there were adequate controls in place to ensure that the information handling practices of institutions selected were in compliance with the Privacy Act.
Scope
The review covered the activities of five institutions – CSIS, the RCMP, CBSA, GAC, and IRCC – for the one-year period August 1, 2015 through July 31, 2016. The review was conducted largely by way of interview, and through the review of documentation supplied by institutional officials. In addition to the review of records of disclosure for the period under examination, our review included an evaluation of institutional policies, procedures, and internal controls. The review did not include an examination of information technology systems supporting SCISA-related disclosures.
The review was substantially completed by March 31, 2017.
Criteria
Review criteria were derived from the Privacy Act, along with associated Government of Canada policies, directives, standards and guidelines related to the management of personal information.
The review was conducted with a view to determining the following:
- Whether information disclosed pursuant to SCISA fell within the definition of an activity that undermines the security of Canada, and was relevant to the recipient institution’s mandate;
- Whether information that did not meet legislative or regulatory requirements was segregated, returned, or securely disposed of;
- Whether records of all disclosures under SCISA were kept, including written records of what was disclosed, to whom, and why;
- Whether information exchanged between institutions was subject to a written information sharing agreement;
- Whether information disclosed by institutions was subject to appropriate internal controls and oversight; and
- Whether potential privacy risks associated with the sharing of information under SCISA had been appropriately assessed prior to sharing personal information.
Standards
The review was conducted in accordance with the legislative mandate, policies and practices of the Office of the Privacy Commissioner of Canada, and followed the spirit of the audit standards recommended by Chartered Professional Accountants of Canada.
Appendix A: Entity responses to recommendations:
Canada Border Services Agency
| Recommendation | Response |
|---|---|
| To encourage good governance over the sharing of personal information under SCISA, and to improve accountability and transparency with respect to its use, institutions should, in collaboration with their partners, implement a formal and standardized process for the identification and recording of information sharing activities under the Act. | The CBSA accepts this recommendation. Processes are already in place for such tracking, and the CBSA anticipates it will apply continued improvements towards formal and standardized tracking of its information sharing activities in tandem with any requirements set out in Bill C-59 and potentially related future regulations. All improvements will be implemented within the scope of the CBSA’s technical capacity. |
| Recordkeeping practices of disclosing institutions should meet the minimum standards set out in Public Safety Canada’s Deskbook, and include a detailed description of how the facts of a given situation meet the legal grounds for disclosure. | The CBSA accepts this recommendation. The CBSA will ensure appropriate policy guidance is in place to ensure that rationales for information disclosure or intake decisions will be provided as necessary and provide sufficient detail to satisfactorily inform experts who have some contextual knowledge such as judges, prosecutors, lawyers and investigators, as to why a particular decision was made. |
| Institutions should review and, where appropriate, adjust internal governance instruments to ensure that information sharing under SCISA complies with legislative requirements. | The CBSA accepts this recommendation. The CBSA regularly conducts review of its information sharing activities along with providing real-time policy guidance for more complex disclosure decisions. Relevant policy documents are updated or adjusted as required to address changing operational realities and ensure guidance is based on the latest developments in federal law, such as future requirements in Bill C-59 and potential future amendments to the Privacy Act. |
| Institutions should ensure that policies governing information exchanges under SCISA are supported by commensurate internal controls. | The CBSA accepts this recommendation. The CBSA will continue to review and evolve its current practice of requiring that all disclosures of information be approved at the appropriate levels. Moreover, the CBSA regularly provides tailored training to officials who disclose information to ensure they have a level of knowledge to which accountability can be applied. |
| Institutions should ensure that written agreements governing the disclosure and receipt of information under SCISA include appropriate privacy protections. | The CBSA accepts this recommendation. It is the CBSA’s current practice, as agreements or arrangements are implemented or renewed, to ensure these documents include appropriate privacy protections such as caveats warning against onward disclosure, an obligation to correct information, and to report any privacy breaches involving specific information to the entity that provided the information so that appropriate remedies can be applied. Other provisions may include auditing arrangements between the participants in an arrangement or parties to an agreement. |
| In keeping with the requirements of the Government of Canada’s Policy on Privacy Protection, and its supporting Directive on Privacy Impact Assessment, institutions sharing or receiving personal information pursuant to SCISA should undertake a formal assessment of the privacy impacts associated with its operationalization. | The CBSA accepts this recommendation. The Security of Canada Information Sharing Act conveys no new collection authorities, so there is no expansion or change in the existing mandate of the CBSA, nor any other entity that may use SCISA. Notwithstanding, the CBSA agrees that it will assess the need, in coordination with Public Safety, of including SCISA in PIAs that relate to the programs of the Agency where information is shared under SCISA. |
Canadian Security Intelligence Service
| Recommendation | Response |
|---|---|
| To encourage good governance over the sharing of personal information under SCISA, and to improve accountability and transparency with respect to its use, institutions should, in collaboration with their partners, implement a formal and standardized process for the identification and recording of information sharing activities under the Act. | The Service accepts this recommendation. All CSIS disclosures are conducted pursuant to s. 19 of the CSIS Act and not pursuant to SCISA. While the obligation to record disclosures resides with the disclosing institution, the Service has nevertheless developed and initial approach to record information received under SCISA from other partners. The Service will review its approach and update as required. |
| Institutions should implement policies and procedures or adjust existing governance instruments to ensure that all information sharing activity under SCISA complies with legal requirements. | The Service accepts this recommendation. The Service’s approach to operationalizing SCISA, as briefed to the OPC in advance of implementation, was to adopt a strategic bilateral approach to engaging partners to ensure a responsible exercise of this authority. Global Affairs Canada and the Canada Revenue Agency were identified as priority partners. The Service and Global Affairs Canada worked jointly to develop a governance framework. This included the development of joint communication material to employees; a written information sharing arrangement identifying what information can be disclosed as well as how the information will be managed and used; standardized templates to facilitate disclosures of information; and joint training initiatives to familiarize employees with all related requirements. Efforts remain underway with the Canada Revenue Agency to develop a written information sharing arrangement to govern disclosures under SCISA. Further to this recommendation, CSIS will review, over the course of the next fiscal year, all guidance documentation and update, as necessary. CSIS will also develop new material as required. |
| Institutions should ensure that policies governing information exchanges under SCISA are supported by commensurate internal controls. | The Service accepts this recommendation. While CSIS does not disclose information under SCISA, it has an obligation to ensure that all information received under SCISA from partners meets the requirements of the CSIS Act. To ensure this occurs CSIS has developed a specific process for managing pro-active disclosures from partners. Specifically, CSIS has designated a specific branch to act as a single point of contact, which represents an internal control on the initial access and use of the information. In relation to disclosures received further to a CSIS request for information, CSIS applies, and will continue to do so, relevant policies and procedures governing the use, management and access of information. Further to this recommendation, CSIS will assess whether a specific policy or procedure on SCISA is required. |
| Institutions should ensure that information sharing activity under SCISA is subject to a written agreement. | The Service partially accepts this recommendation. The Service assesses the requirement for a written information sharing agreement on a case-by-case basis, and will continue to do so. To date, as noted to the OPC during the review process, CSIS has identified the requirement for a written arrangement with both Global Affairs and the Canada Revenue Agency. The one with Global Affairs Canada has been signed and the one with the Canada Revenue Agency is being finalized. |
| Institutions should ensure that written agreements governing the disclosure and receipt of information under SCISA include appropriate privacy protections. | The Service accepts this recommendation. The aforementioned ISAs include provisions relating to privacy protections, including as it pertains to the use and management of information disclosed. Where additional ISAs are developed, the Service will ensure that appropriate privacy protections are included in all the written agreements governing the receipt of information under SCISA. |
| In keeping with the requirements of the Government of Canada’s Policy on Privacy Protection, and its supporting Directive on Privacy Impact Assessment, institutions sharing or receiving personal information pursuant to SCISA should undertake a formal assessment of the privacy impacts associated with its operationalization. | The Service partially accepts this recommendation. Over the next year, CSIS will undertake a formal assessment to determine whether a privacy impact assessment is required for its operationalization of SCISA. |
Global Affairs Canada
| Recommendation | Response |
|---|---|
| To encourage good governance over the sharing of personal information under SCISA, and to improve accountability and transparency with respect to its use, institutions should, in collaboration with their partners, implement a formal and standardized process for the identification and recording of information sharing activities under the Act. | Accept. Global Affairs Canada has established processes whereby each disclosure undergoes a rigorous review, including legal consultation, prior to being released. We will continue to review existing processes with our partners over the next year and strive toward a more standardized process for the identification and recording of information-sharing activities under the Act. |
| Recordkeeping practices of disclosing institutions should meet the minimum standards set out in Public Safety Canada’s Deskbook, and include a detailed description of how the facts of a given situation meet the legal grounds for disclosure. | Accept. Global Affairs Canada has created a repository to keep track of all SCISA incoming requests as well as our outgoing responses. Over the next year we will review our recordkeeping practices with a view to enhancing this procedure to also include a written description of the rationale for disclosure and how the legal threshold for disclosure has been met. |
| Institutions should review and, where appropriate, adjust internal governance instruments to ensure that information sharing under SCISA complies with legislative requirements. | Accept. One of our internal governance practices currently in place to ensure compliance with SCISA is systematic consultation with our legal bureau on each decision to disclose. Over the next year we will examine whether additional work is required to adjust or enhance governance instruments. It should be noted that the recently tabled Bill C-59 includes proposed additional considerations pertaining to the operationalization of SCISA (including publishing the national security mandate of each institution; publishing the delegation authority; and establishing a centre of expertise for all institutions for awareness/training/best practices). We will continue to follow this and other potential changes to ensure compliance with legislative requirements. |
| Institutions should ensure that policies governing information exchanges under SCISA are supported by commensurate internal controls. | Accept. Currently, each decision to disclose must be documented and approved by a Director or Director General and tracking (incoming and outgoing) is conducted by means of an electronic repository. Over the next year we will examine the need for an overarching policy document to include the various operating procedures already in place (tripartite direction to missions; updated consular manual; consular PIA, Information Sharing Agreement with CSIS, etc.). |
| Institutions should ensure that written agreements governing the disclosure and receipt of information under SCISA include appropriate privacy protections. | Accept. Our Consular Information Sharing Agreement with CSIS contains a number of privacy protections. Over the next year, we will explore developing a similar consular information sharing agreement with the RCMP, and we will work to ensure that appropriate privacy protections are in place. We will also continue to review whether other programs require information sharing agreements. |
| In keeping with the requirements of the Government of Canada’s Policy on Privacy Protection, and its supporting Directive on Privacy Impact Assessment, institutions sharing or receiving personal information pursuant to SCISA should undertake a formal assessment of the privacy impacts associated with its operationalization. | Accept. It is important to note that all but one of our SCISA disclosures thus far have been from our consular program. A Privacy Impact Assessment has already been completed by the consular program and fully applies to SCISA, as it does to all consular operations’ decisions to disclose based on other authorities. A Privacy Impact Assessment has been initiated for our mission security program. We will continue to review the need for any additional Privacy Impact Assessments. |
Immigration, Refugees and Citizenship Canada
| Recommendation | Response |
|---|---|
| To encourage good governance over the sharing of personal information under SCISA, and to improve accountability and transparency with respect to its use, institutions should, in collaboration with their partners, implement a formal and standardized process for the identification and recording of information sharing activities under the Act. | IRCC accepts the recommendation. IRCC welcomes the recommendation for a formal and standardized process for the identification and recording of information sharing activities across institutions. IRCC is committed to encouraging good governance, while improving accountability and transparency with respect to the sharing of information under SCISA. IRCC has implemented a system to track SCISA-related disclosures which involves manually tracking key information regarding each disclosure or receipt under SCISA, keeping a copy of the information disclosed, and using letters to request and disclose information. To support this system, IRCC provides training on disclosures under SCISA and receipt of information under SCISA. IRCC also welcomes the proposed amendment to the SCISA under Bill C-59 to provide to the National Security Intelligence Review Agency after the end of each calendar year a copy of every record prepared with respect to its disclosures under the Act. |
| Recordkeeping practices of disclosing institutions should meet the minimum standards set out in Public Safety Canada’s Deskbook, and include a detailed description of how the facts of a given situation meet the legal grounds for disclosure. | IRCC accepts the recommendation. IRCC recognizes the importance of transparent recordkeeping practices and endeavours to continue improving its recordkeeping practices. IRCC has implemented a system to track SCISA-related disclosures which involves manually tracking key information regarding each disclosure or receipt under SCISA, keeping a copy of the information disclosed, and using letters to request and disclose information. IRCC has also developed step-by-step guidelines to guide the analytical process required on a case-by-case basis to ensure disclosure and receipt of information meet the legal grounds for disclosure. |
| Institutions should ensure that policies governing information exchanges under SCISA are supported by commensurate internal controls. | IRCC accepts the recommendation. IRCC has taken steps to ensure that it has commensurate internal controls to support its information sharing activities under SCISA and the related policies governing the exchange of information. IRCC has an internal policy to support the operationalization of SCISA which the OPC has reviewed and described as very sound. The policy provides guidelines on internal controls including the use of caveats, secondary disclosure and recordkeeping. Step-by-step guidelines have been prepared to guide IRCC employees when disclosing information under the Act or when receiving information disclosed pursuant to the Act to ensure the proper review of disclosures and receipts by designated employees. |
| Institutions should ensure that written agreements governing the disclosure and receipt of information under SCISA include appropriate privacy protections. | IRCC accepts the recommendation. IRCC recognizes the importance of having sufficiently robust and comprehensive information sharing agreements. IRCC has incorporated SCISA into an information sharing arrangement with an institution to cover the exchange of information under the Act and will engage with key partners to which it discloses information on a more regular basis, as existing information sharing arrangements are being renegotiated. |
| In keeping with the requirements of the Government of Canada’s Policy on Privacy Protection, and its supporting Directive on Privacy Impact Assessment, institutions sharing or receiving personal information pursuant to SCISA should undertake a formal assessment of the privacy impacts associated with its operationalization. | IRCC accepts the recommendation. IRCC acknowledges the importance of developing, maintaining, and publishing privacy impact assessments (PIAs) in relation to new programs and services involving personal information. In the context of SCISA, the instances of information sharing were infrequent and did not substantially modify IRCC’s programs or activities. SCISA provides an efficient mechanism to share targeted information that would likely have been shared with security partners in the past as well, however through a more burdensome process. Notwithstanding the above, IRCC recognizes the privacy implications associated with disclosing personal information for national security purposes. |
Royal Canadian Mounted Police
| Recommendation | Response |
|---|---|
| To encourage good governance over the sharing of personal information under SCISA, and to improve accountability and transparency with respect to its use, institutions should, in collaboration with their partners, implement a formal and standardized process for the identification and recording of information sharing activities under the Act. | Agree. Federal Policing will amend its Operational Manual to require that the following pieces of information be recorded for all disclosures made by the RCMP pursuant to SCISA:
|
| Institutions should review disclosures received under SCISA to ensure that the information contained therein is relevant to its jurisdiction or responsibilities in respect of activities that undermine the security of Canada, and not retain any information that does not meet that threshold. | Agree, in part. Federal Policing personnel will continue to engage with partners to ensure that information disclosed is targeted and specific to the individual(s) in question. Further, management teams of Federal Policing and CBSA have agreed to issue a joint communiqué to staff to, among other things, reiterate the importance to keeping disclosures targeted and specific. |
| Institutions should review and, where appropriate, adjust internal governance instruments to ensure that information sharing under SCISA complies with legislative requirements. | Agree. The RCMP will review the Operational Manual to validate that information sharing under SCISA complies with legislative requirements. Updates, if required, will be made to the Manual and internally communicated accordingly. |
| Institutions should ensure that policies governing information exchanges under SCISA are supported by commensurate internal controls. | Agree. The RCMP will review the Operational Manual to validate that information exchanges under SCISA are supported by commensurate internal controls. Updates, if required, will be made to the Manual and internally communicated accordingly. |
| Institutions should ensure that written agreements governing the disclosure and receipt of information under SCISA include appropriate privacy protections. | Agree, in part. The RCMP will review the Operational Manual to validate that the caveats applied to all information disclosed under SCISA are appropriate. Updates, if required, will be made to the Manual and internally communicated accordingly. |
| In keeping with the requirements of the Government of Canada’s Policy on Privacy Protection, and its supporting Directive on Privacy Impact Assessment, institutions sharing or receiving personal information pursuant to SCISA should undertake a formal assessment of the privacy impacts associated with its operationalization. | Agree. The RCMP will complete a Privacy Impact Assessment of its receipt and disclosure of information under SCISA. |
- Date modified:

