Immersive Technology: Takeaways from the 2023-24 OPC Contributions Program theme projects

Read more

Read more

Read more

Read more

On Friday, March 10, 2017, the Behavioural Economics in Action at Rotman (BEAR) group at the University of Toronto will bring together academics, researchers, regulators, and industry and consumer groups alike to address consumer privacy challenges in the online world.
Read more
Virtual Private Networks (VPNs) let you establish a secure communications channel between your computing device and a server. After connecting to the server, you could gain access to a private network that has work files or applications, or use the server as a relay point to then access Internet content when browsing from a public network.
Read more
Canadians’ mobile devices are filled with applications that collect personal information, including identifiers that are engrained into different parts of the devices. But what exactly are these identifiers, and how are they used?
Read more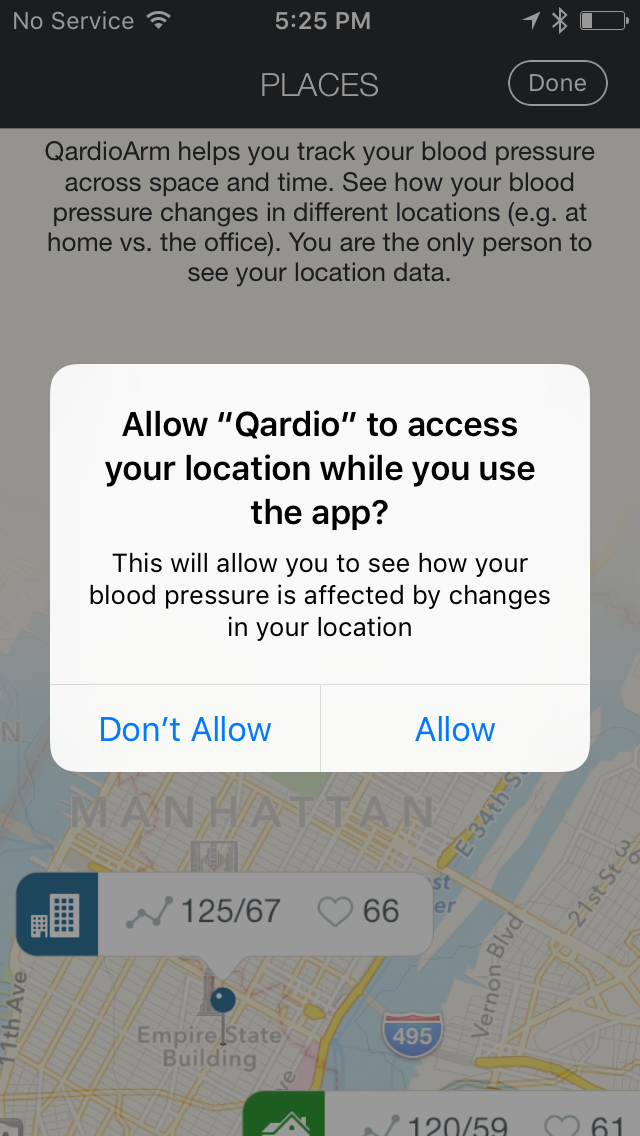
Smart TVs . . . Fitness trackers . . . Automated thermostats . . . Self-driving cars . . .
Read more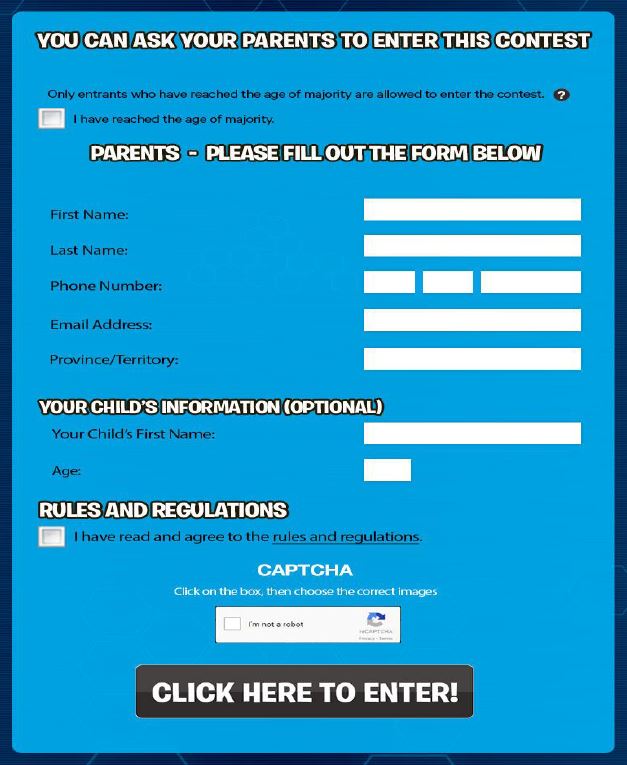
So whatever happened with that Children’s Privacy Sweep, you ask?
Read more
We all encounter scores of user agreements when we go online. Do you read the full terms and conditions governing your use of a site, or do you just hit the "I accept" button and surf on?
Read more
Our Office recently concluded an investigation that has resulted in two important firsts along with some key lessons learned for businesses conducting e-mail marketing.
Read moreShowing items 1 through 10 of 38.